Bienvenue sur la page RZO
Ressources de Jean et Pierre Parrend en informatique, telecoms et reseaux
Principles of OSGi bundles signatureThis technical note is a short version of INRIA Technical Report n°0323. The OSGi platform provides support for the life cycle of bundles, from installation through execution to removal. This implies that the security for OSGi must be considered along the whole life-cycle, and in particular that the deployment is taken into account. Security implies three main aspects:
The OSgi specification propose to enforce the first two properties: Integrity and Authentication, that can not be considered separately. In fact, guaranteeing integrity without authentication means that anybody can provide the data, and authentication without integrity means that anybody can change the data. Confidentiality is not considered, because it implies that security unaware systems are excluded. We present here the principles of secure deployment, the threats that exist, and the solution proposed by the OSGi specification. The structure of a signed bundle as well as the algorithm for signing and validating a bundle are shown.
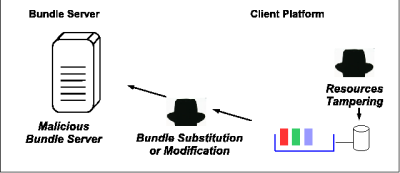
These mechanisms are derived from the Jar archive specification, and can be applied to any type of data or code archive that is transfered over an unsecure network. Threats to the DeploymentMajor security threats during deployment are of three types. The first type is the presence of malicious bundle publication servers.
So as to protect the component platform from the first two threats, it is necessary to control that the bundle publishers are trustworthy, and that loaded bundles have not been tampered with during the transfer over an untrusted network, such as the Internet. Structure of a signed bundleBecause of the particular constraints on the signature of a bundle, it is necessary to store it and all related resources in the bundle itself. Moreover, it is mandatory that multiple signers can sign the same bundle.
The Manifest file of the archive (1) contains the hash value of each resource in the archive. To support several signers, the digital signature is applied not directly on the Manifest file, but on a so-called `Signature File' (2), which is specific to each signer. A hash value of the Manifest file must be included. The digital signature of this Signature File is stored along with data that are necessary for its validation in a CMS file of type `signed-data' which is named `Signature Block File' (3). This structure of a signed bundle will be enlightened by a simple example of the HelloWorld bundle, whose signer is named PIERREP. This bundle contains three classes: HelloWorldActivator (the activator, or starter, of the bundle), HelloWorldInterface (the definition of the HelloWorldInterface service that is provided by the bundle), and HelloWorldImpl (the implementation of the above mentioned service). The meta-data of the bundle are the following. First, the Manifest file, MANIFEST.MF, which contains meta-data specific to OSGi bundles, as well as the hash value of all resources. Secondly, the Signature File, PIERRE.SF, contains the hash value of the Manifest file. Thirdly, the Signature Block File, PIERRE.DSA, is a CMS file that contains the digital signature of the Signature File, and the public key certificate of the signer. They must be stored in this order (and before all other resources) in the bundle archive.
Algorithms for bundle signatureThe process of signing bundle must create bundle meta-data that are compliant with presented specifications. Bundle Signature Generation
The main steps of bundle signature generation are the following.
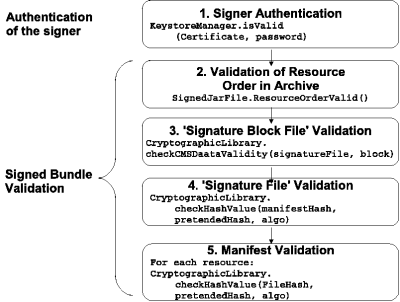
Bundle Signature Validation
ConclusionSecuring the deployment of components implies to protect the execution platform from malicious component publishers, and from potential modifications of the components after their publication. LinksInternal linksFurther references |
|||||||||||||||
Last update : 22 April 2008 - contact the webmaster