Signing Java Archives with the Jarsigner Tool
This technical note will show you how to sign Jar files with the sun utilities, and how to handle related cryptographic keys.
You will find here informations related to following topics:
Most of the information in this note can be found in the `help' section of the jarsigner and keytool utilities:
jarsigner --help
keytool --help
Criteria for Signature Validity
The criteria of validity of a digital signature are the following:
- No modification of the archive resources after the signature
- certificate not outdated (not not yet valid)
Moreover, the signer of the archive must be known, i.e. its public key certificate must be identified as trusted before the validation. Otherwise, any malicious third party can forge a similar certificate, potentially with the same signer name, and present a coherent signed archive.
Additional criteria of archive signature validity are defined in the context of the OSGi framework, that are specific to the deployment of components from third party repositories:
- No resource removed from the archive after the signature
- No resource added from the archive after the signature
- The digital signature must immediately follow the Manifest file of the archive, to prevent caching malicious files
This means that according to the security level you need, the Sun criteria of signature validity may not be sufficient.
Use of the JarSigner Tool
The Sun `Jarsigner' is a utility delivered along with Sun JDK. It has the ability to sign Java Archives (Jars), and to verify the validity their signature.
The use of the Sun Jarsigner tool is highlighted with an example of an OSGi test bundle called fridgebundle-1.1.jar. OSGi archives are a specific type of jar files.
So as to test the jarsigner tool, you need to have a public/private key pair. The example are given with Bob's key pair.
- If you want to make the tests with Bob's key pair, download the keystore file named testkeystore. Store it in the
refArchive directory.
- If you want oto create your own public/private key pair, see the paragraph relative to the keytool utility to learn about it.
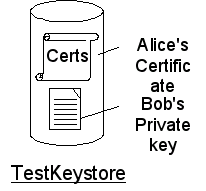
Following operations can be performed with the jarsigner tool. Create a refArchive directory, and store each example bundle in it:
- Sign a given jar archive, refArchive/fridgebundle-1.1.jar, with bob's private key
jarsigner -keystore refArchive/testkeystore -signedjar refArchive/fridgebundle-1.1.signed.jar refArchive/fridgebundle-1.1.jar bob
Enter Passphrase for keystore: password
Enter key password for bob: bobspwd
- Some test with an invalid archive signature, refArchive/bindex-manifestMainAttrsModified-1.0.jar:
jarsigner -verify refArchive/bindex-manifestMainAttrsModified-1.0.jar
jarsigner: java.lang.SecurityException: Invalid signature file digest for Manifest main attributes
Remark: No warning is issued by the Sun Jarsigner if the signer of the archive is unknow to you. No matter who has signed the archive, this latter will be considered as valid !
Use of the Keytool Utility
The Sun keytool utility supports the management of DSA and RSA asymetric key pairs, as well as the management of public key certificates of third party actors.
Requirements:
- have a keystore file
Example: the keystore file is named testkeystore, and is accessible with the password password. In our example, it is stored in the refArchive/ directory.
If you specify a keystore that does not exist in the keytool options, it is automatically created and initialized with the given parameters (e.g. the password).
The default keystore in *nix systems is /home/user/.keystore. It is overridden by the -keystore option.
You can perform following tests so as to learn how to use the keytool:
- Create a new DSA Key Pair for Bob
keytool -genkey -keystore refArchive/testkeystore -alias bob
password: password
- The default algorithm for Key Pairs is DSA. The
-sigalg option can be set to generate other types of keys, such as DSA ones.
- The Distinguished Name for Bob is:
CN=Bob, OU=testing, O=signer & Co., L=wonderland, ST=United Kingdom, C=UK
the password for accessing to the private key of Bob is:
bobspdw
- Visualize the content of the keystore
keytool -list -keystore refArchive/testkeystore
- which will show something like this if the keystore has just been created:
Keystore type: jks
Keystore provider: SUN
Your keystore contains 1 entry
bob, Jan 28, 2007, keyEntry,
Certificate fingerprint (MD5): 5C:B4:82:80:46:5D:C1:0B:48:DE:B6:50:F0:22:24:9D
- Extract of the public key certificate of Bob for dissemination. The certificate is stored in the
bob.cert file
keytool -export -keystore refArchive/testkeystore -alias bob > refArchive/bob.cert
- If Bob want that the world can check whether he is the one which signs Jar files, he has to make his public key available to them.
- Visualize a certificate
keytool -printcert -file refArchive/bob.cert
-
which will sow you something like:
Owner: CN=Bob, OU=testing, O=signer & Co., L=wonderland, ST=United Kingdom, C=UK
Issuer: CN=Bob, OU=testing, O=signer & Co., L=wonderland, ST=United Kingdom, C=UK
Serial number: 45bd17a6
Valid from: Sun Jan 28 22:37:42 CET 2007 until: Sat Apr 28 23:37:42 CEST 2007
Certificate fingerprints:
MD5: 5C:B4:82:80:46:5D:C1:0B:48:DE:B6:50:F0:22:24:9D
SHA1: 2D:32:03:BF:39:74:B0:00:71:5A:14:F7:E7:85:18:8D:C7:42:DC:3B
- Import a certificate, e.g. the one of alice
- Store the Certificate of Alice into the
refArchive/ directory: alice.cert.
keytool -import -keystore refArchive/testkeystore -file refArchive/alice.cert -alias alice
password: password
Trust this certificate? [no]: yes
- Bob may want to communicate with Alice. He needs to import her Public Key Certificate into his own keystore, and mark it as `trusted'.
- Visualize the content of the keystore
keytool -list -keystore refArchive/testkeystore
Enter keystore password: password
-
Which shows you something like:
Keystore type: jks
Keystore provider: SUN
Your keystore contains 2 entries
alice, Jan 28, 2007, trustedCertEntry,
Certificate fingerprint (MD5): 01:29:74:E3:51:9E:31:87:0E:AB:C4:5C:0B:6B:34:03
bob, Jan 28, 2007, keyEntry,
Certificate fingerprint (MD5): 5C:B4:82:80:46:5D:C1:0B:48:DE:B6:50:F0:22:24:9D
-
Two different types of entries are available:
- a trustedCertEntry, which contains the Public Key Certificate of alice
- a keyentry, which contains the public/private key pair of Bob
Alternatives
The SF-Jarsigner tool is a graphical utility for signing jars. It has been developped to publish OSGi bundles, but can be used to simply sign Jar archives.
You will find here an illustrated tutorial for using SF-Jarsigner to sign Jats.
References
You can find further informations here:
|
